WAF bypass made easy
In this post I will share my testing experiences about a web application protected by a web application firewall (WAF). The investigation of the parameters of web interfaces revealed that I can perform XSS attacks in some limited ways. The target implemented blacklist-based filtering that provided some HTML tag and event handler restriction. Since this restriction appeared at quite unusual places I suspected that there might be a WAF in front of the application. To verify my suspicion:
- I tested the interfaces by random HTTP parameters which contained XSS payload. Most of the time a WAF checks all of the input parameters but the server side validation only checks the expected ones;
- I used the Wafit tool.
These tests underpinned my assumption: there was indeed some application level firewall in front of my target.
In order to map the filter rules I created a list of HTML4 and HTML5 tags and event handlers based on the information of w3.org. After this I could easily test the allowed tags and event handlers with Burp Suite Professional:
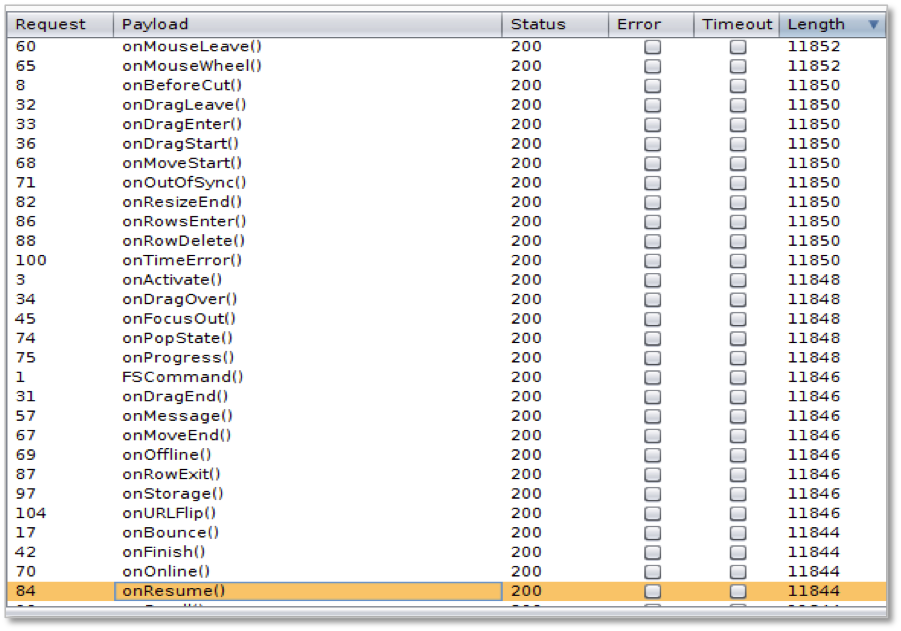
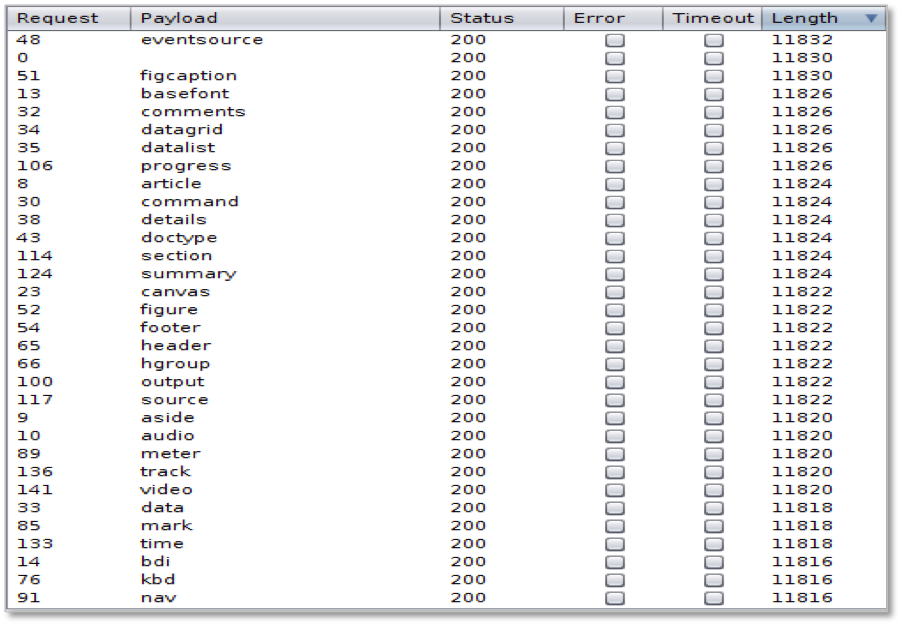
Based on the results we can perform only some browser specific attacks typically against IE/6.0. However, many web applications handle parameters passed by GET and POST methods in the same way. I performed the tests again, now submitting the crafted parameters in the HTTP POST body and found that the WAF didn’t interrupt my request and the application processed my input through the same vulnerable code path. This way I could perform XSS without limitation and surprisingly was able to find an SQL injection issue also.
When you try implement a WAF in your infrastructure the most important key concepts are:
- Know your system: Collect the applications and HTTP parameters to be protected and understand how they are used (data types, expected format, etc.);
- Consult somebody with an offensive attitude (like a penetration tester) before you implement the defense;
- Be aware of the limits of blacklist-based filtering;
Improper WAF implementation can lead to false sense of security that can result in more damage than operating applications with known security issues.