
Banging 3G rocks
I’ve always wanted to take a look at the security of 3G modem sticks but as a more “high-level” guy, I basically procrastinated the task of messing with kernel drivers and such, and settled to installing these devices into disposable virtual machines for security.
But after I saw the presentation of Nikita Tarakanov about the modems of Huawei (slides here) I realized that many interesting things can be found out by using rather simple techniques. So I grabbed the first stick in sight and started to investigate how the userland part of its installed software works.
The stick is an ONDA Communications MF195 (product of ZTE), provided by T-Mobile. It works pretty well with Windows and OS X, unfortunately for me, I couldn’t get it to work under Linux :(
As it turns out, the situation with ZTE is quite similar to Huawei, in that they both have issues with file permissions. The installed software has numerous configuration options for external URL’s, for example, here is the content of [SW home]/Bin/UpdateCfg.ini:
[UPDATE]<br></br>ENABLE_UPDATE=1<br></br>UPDATE_FREQUENCE=336<br></br>[Service]<br></br><strong>ServiceURL=https://tmobile.ztems.com/UpdateEntry.aspx</strong><br></br><strong>UpdateReport=https://tmobile.ztems.com/UpdateResultReport.aspx</strong><br></br>ServicePort=443<br></br>UPDATE_PATH=./download<br></br>RETRY_CONNECT=300<br></br>RETRY_SLEEP=1<br></br>CONNECT_TIMEOUT=20<br></br>[UpdateMode]<br></br>BranchItem=TMO_III_DE
And yes, this file is writable by any user, along with the main executable that is started at every login with the privileges of the logged in user creating a trivial way for local user impersonation or privilege escalation:
We have to note though, that this is still better than Huawei’s ouc.exe that is also “world” writable and runs as a SYSTEM service…
After these little games I started to wonder if I could backdoor the stick by changing the installer. I used a different stick, an out of use ZTE K3570-Z from Vodafone for this task, because I felt that I could easily brick the MF195 which I use regularly.
The task sounds trivial: the device shows up as a USB CD-ROM drive when plugged in without the proper drivers installed, so all we have to do is to change the contents of this virtual optical drive.
But there are some problems: first of all, installation fails most of the time even with the original software that makes testing really painful. The filesystem is iso9660 that is read-only by design, so we have to first repack the FS contents before reflashing, but this should be a trivial task. The biggest problem is to force the OS to write something to a device that it knows to be a read-only CD-ROM. For this task I had to use the dc-unlocker tool that is proprietary, pirate-ish and needs paid registration (unless you find some “demo” codes on the web, that you obviously wouldn’t want to do…), so a more open solution for this would be highly appreciated.
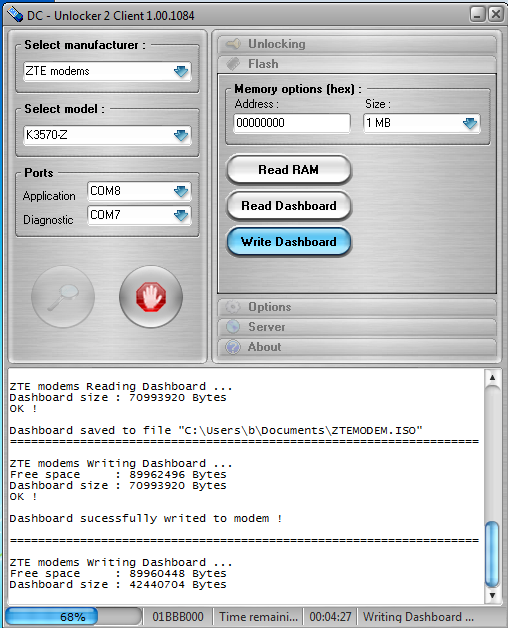
I managed to take the fail train for about an hour because I didn’t read the instructions on the screen, so if you plan to do similar things yourself, spare yourself some time and RTFM. The COM port settings can be figured out from the device manager after the drivers are loaded, and you may also need to enable the diagnostics port using the menu option of the Unlock tab of the dc-unlocker.
I could extract the installer image using dd, mounted the image as a loop device, changed a few things for a proof-of-concept, then created a new image using mkisofs that I wrote out using dc-unlocker (the Flash writing feature is free). In order to get the stick work again, you have to disable the diagnostics port after the new image is written out.
This way I managed to place arbitrary contents on the virtual drive of the stick. I used msfvenom to plant custom payload into the original installer so keeping the whole device working. Since the binaries supplied by the vendor/service provider is not digitally signed this change wouldn’t be noticed by the victim in a real situation.
Aside from satisfying my curiosity, this method could be used to create more convincing baits for social engineering projects, and solving the problem of potential network restrictions in one shot.
Also a malware could ensure its persistence by maintaining a copy of itself on the attached USB modems. The hard part of this latter case is that rewriting the image on the stick takes quite long (a typical image is written out in around 10 minutes), and different hardware would probably need different infection methods.
While I don’t find the discussed vulnerability particularly dangerous, portable cellular modems are great examples of the tendency that we blindly trust every hardware – no matter how easily it can be backdoored – if it has a nice casing with a vendor logo printed on it.
If you managed to extract some interesting info about your modems don’t hesitate to share it with us in the comments!