
Notes on McAfee Security Scan Plus RCE (CVE-2017-3897)
At the end of last month, McAfee published a fix for a remote code execution vulnerability in its Security Scan Plus software. Beyond Security, who we worked with for vulnerability coordination published the details of the issue and our PoC exploit on their blog. While the vulnerability itself got some attention due to its frightening simplicity, this is not the first time SSP contained similarly dangerous problems, and it’s certainly not the last. In this post, I’d like to share some additional notes about the wider context of the issue.
Although I’m generally focused on security software, the main motivation for researching this product was that it is distributed as adware a promotional software bundled with the free products of Adobe, such as Flash Player or Reader DC (the installer configuration depends on the client browser/OS):
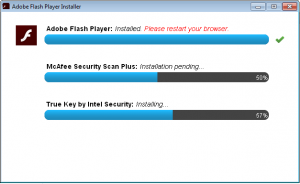
The remote command execution is achieved via the LaunchApplication() JavaScript API that was added as an extension by the vendor to the standard browser frame that displays numerous UI elements. While it may seem difficult to comprehend why adding such an API was a good idea, the application actually uses this feature at least when it first launches the installed application after the user accepted the license agreement:
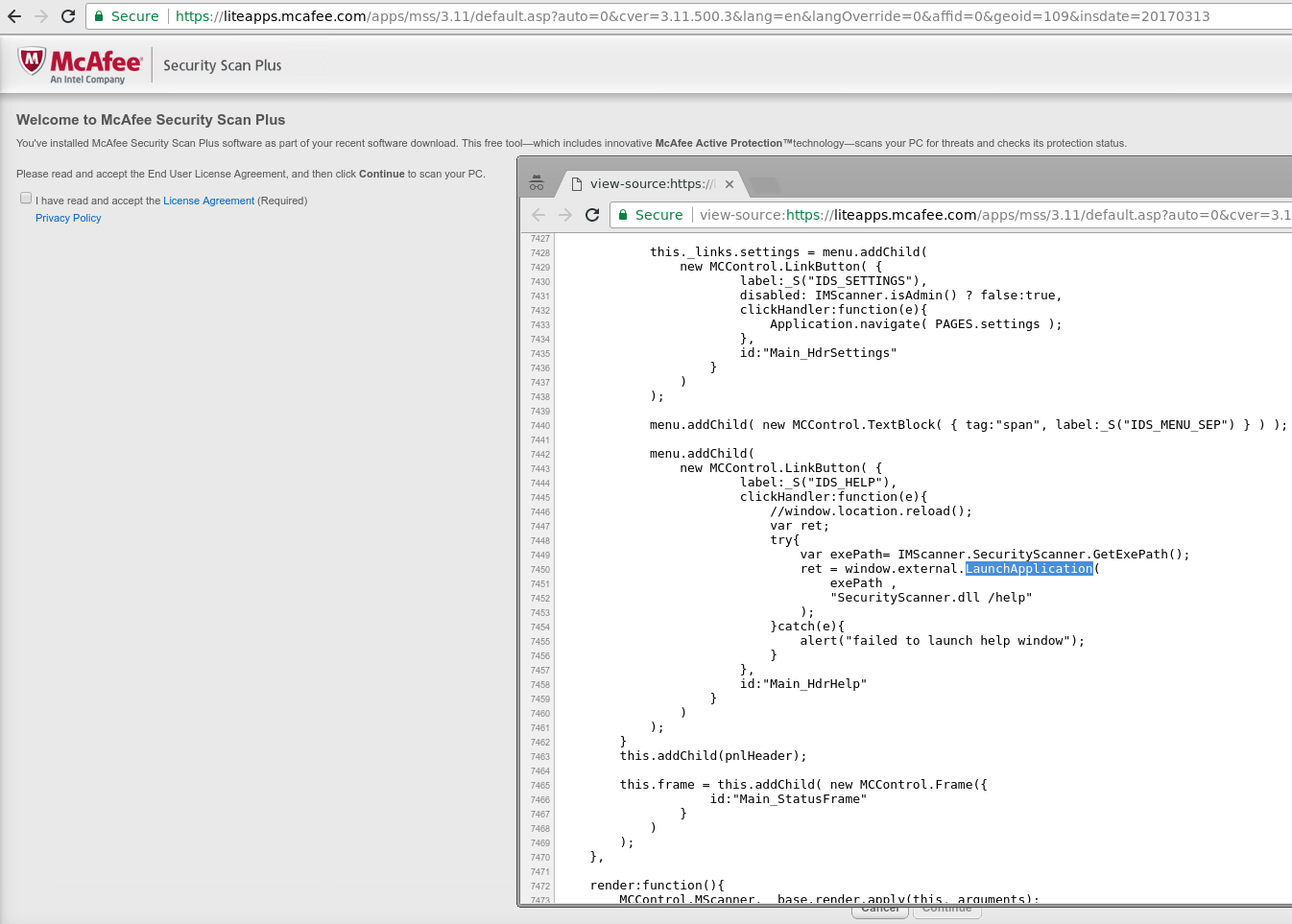
Because of this, the API (and its relatives like LaunchAppAsUser() or LaunchBrowser()) was not removed from the patched version.
The official advisory states that “an active network adversary could execute an existing malware executable in the system”. It should be obvious though that it doesn’t require any “existing malware” to do evil things on the target by invoking cmd.exe, PowerShell, etc. (multiple commands and arguments can be trivially provided, as it can be seen below).
The advisory also states that “as part of this fix, McAfee removed the McAfee Security Scan Plus bottom banner dependency from http://home.mcafee.com/”. But since right after installation the software still retrieves files over plain HTTP, it is still possible to exploit the software – although the time window for an attack is much narrower as it was previously:
(“Magas” means “High” integrity level in the Process Explorer)
A basic Google search also shows that at least the following paid products (which partially run with root/SYSTEM privileges) also contain the DLL implementing the same dangerous APIs:
- McAfee Security Center (included in several other products)
- McAfee VirusScan Plus
- McAfee CloudAV
Although my test didn’t identify exploitable HTTP traffic so far in these, some more hidden features or ones to be implemented in the future may contain some surprises.
So in summary:
- McAfee SSP is bundled with highly popular software, most users probably didn’t knowingly install it.
- The software is still exploitable because dangerous APIs and insecure HTTP services are still present. (The risk of this issue is low because of the narrow exploitation window.)
- More McAfee software may be affected by similar issues.
We contacted McAfee PSIRT after the advisory was posted to clarify the current and planned protective measures but got no answer so far.