
Snow cannon vs. unique snowflakes — testing registration forms
Many of the web application tests we conducted had a registration form in the scope. In such cases, there’s usually a field that needs to be unique for each invocation, sometimes called username, in other cases, the e-mail address is used as such. However, launching the Scanner or Intruder of Burp Suite or a similar tool will send the same username over and over again, resulting in possible false negatives. We faced this problem long enough that we came up with a solution for it, and now you can use it too!
Registration forms are not the only culprits, many endpoints implementing custom functionality enforce similar rules regarding uniqueness, a file upload interface is a similar example. Burp already offers a powerful tool for mangling outgoing requests in the form of Session Handling Rules. I already presented this tool in detail in my GWAPT Gold paper and my Camp++ 0x7e0 talk (check out the YouTube recording for a live demo, if you’re into linear media), but it seems, the built-in tools cannot perform anything that makes a request unique. Given two identical requests, it will always perform identical transformations on them.
However, Extender plugins can implement additional session handling actions, thus we could create such a plugin that can make each request unique. The easiest way was to use a simple counter, and since Scanner uses multiple threads by default, AtomicInteger was an easy choice, since it offers the method incrementAndGet, which queries and increments the value in a single atomic step.
There was still a task left, including the value of the counter in each request. I chose regular expressions, which can solve most of the typical situations
that can arise during a web pen testing, and this allowed me to copy both the UI and some of the code from my Commentator plugin with minimal changes. With the extension installed, a new tab called Uniqueness appears with several options:
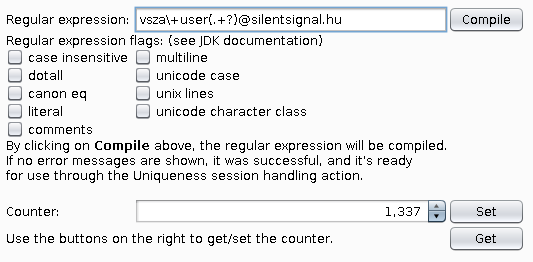
In the above example, anything between user and the @ sign will be replaced in e-mail addresses starting with vsza+user and ending in @silentsignal.hu. If pressing the Compile button doesn’t result in an error message, you’re good to go and can continue to the next step.
In the Session Handling Rules section of the Sessions subtab of the Project options tab, you can add rules that trigger certain actions upon the specified triggers.
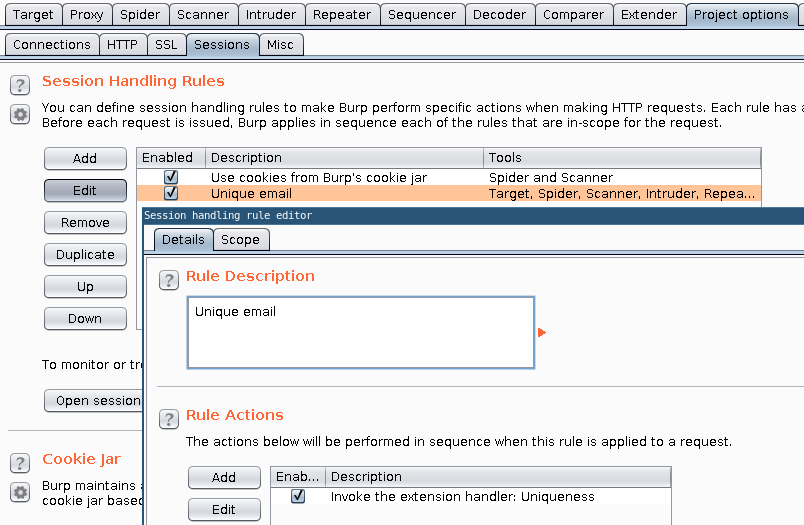
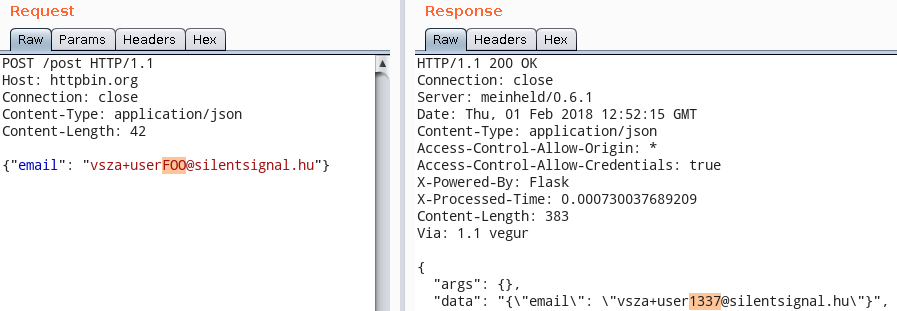
With the session handling rule in place, every tool within the scope of the rule will invoke the magic of this plugin. Below is an example using Repeater.
We hope that this plugin will help pentesters working on web applications do a better job and have one less thing to tackle manually. The source code is available in our GitHub repository under MIT license, feel free to share and improve its functionality. A pre-compiled JAR file can be downloaded from the releases page, which can be added to the Burp Extender directly. Pull requests welcome!
Featured image was taken by Meanmachine.mdp and is available under CC-BY-SA.