Our new tool for enumerating hidden Log4Shell-affected hosts
Log4Shell, formally known as CVE-2021-44228 seems to be the next big vulnerability that affects a huge number of systems, and the affected component, Log4j gets involved in logging untrusted data by design. This results in lots of vulnerable hosts that are hidden in the sense that naive testing won’t find them, as it’s not trivial to know which part of a complex parsing path (potentially involving multiple systems) is vulnerable. We built and released our new open source tool to find these in order to help everyone identify these before the bad guys do.
Traditional behavior-based vulnerability scanning of HTTP interfaces (web applications and APIs) typically involve sending requests to the target and observing its effect. The simplest way is analyzing the response itself, while some vulnerabilities can only be uncovered by observing other side effects. This includes the time it takes to respond, but also any out-of-band interactions.
PortSwigger, the maker of Burp Suite introduced Collaborator in 2015 for the latter, making it easier to detect behavior that had no effect on the response itself. Because of how Log4Shell can be exploited, this already makes detection easier since submitting a hostname as part of the LDAP URL results in DNS requests. However, an even more important consideration is that it makes the detection of those aforementioned hidden hosts possible.
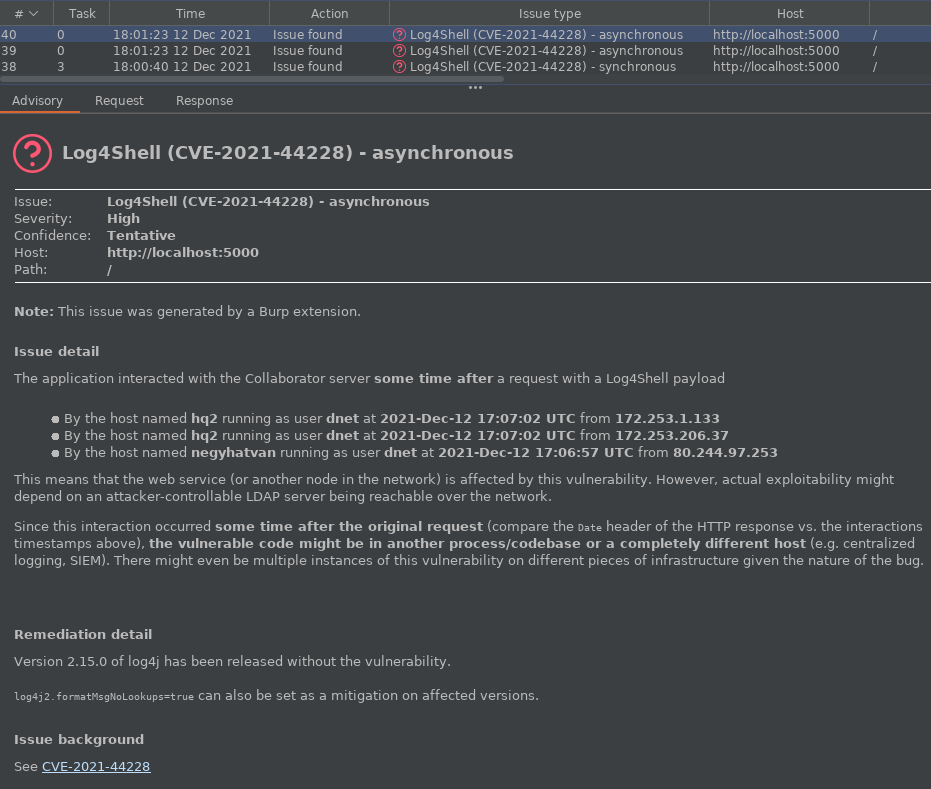
As stated above, traditional HTTP scanning involves request-response loops, based on the idea that even if we monitor out-of-band interaction, interesting server-side processing stops as soon as the response is returned. In case of hidden hosts, vulnerable code might start executing way after the response is sent, either because of latency across distributed systems, or because of batch processing.
We created a Burp Extender plugin that registers itself as an Active scanner check and generates two kinds of payloads. A simpler one includes variable expansion only for the hostname, while a more complex one includes the username as well using USER and USERNAME for compatibility with both Unix-like and Windows operating systems. Synchronous interaction is logged using built-in scanner, while a background thread polls for Collaborator interactions once per minute to test for those hidden hosts and services.
We hope that by excluding code execution functionality, we don’t give the bad guys anything they already don’t have while giving professional pentesters and internal security teams a tool to detect all the hidden vulnerable hosts. Having the hostname and the username is hopefully enough to identify even those processes that are not documented but still processes data at the end of a long pipeline.
The plugin is available in the BApp Store under the name Log4Shell Scanner. It can also be downloaded from our GitHub repository under a GPLv3 license, pre-built JARs can be found on the Releases page, bug reports and pull requests are welcome.
Finally, here’s a short video showing an end-to-end demonstration from downloading and installing the plugin, setting up a single-issue scan (avoiding XSS, SQLi, etc. checks) and detecting both sync and async vulnerabilities.